25 Sept 2025
Discover how default credentials (admin:admin) gave me full access to domain - a shocking security flaw that still exposes businesses in 2025! Learn how to fix this critical vulnerability and protect your systems. #Cybersecurity #BugBounty #ResponsibleDisclosure
Imagine walking up to a bank vault, turning the handle, and finding it unlocked. No alarms, no guards—just free access. That’s exactly what happened when I discovered default credentials (admin:admin) working on redacted.com, a corporate domain that should have been secure.
Because of security reasons i will refer domain name to redacted.com
This wasn’t a sophisticated cyberattack. It was a simple, glaring oversight—one that could have led to data breaches, RCE, or worse
In this post, I’ll Walk you through:
How I found the vulnerability (with screenshots).
Why default credentials are still a massive risk in 2025
How to protect your systems from this rookie mistake
Let’s dive in ....
While testing redacted.com as part of a bug bounty program, I noticed their is a Apache superset running on port 9000 had a generic login page—no CAPTCHA, no rate limiting, just a username and password field
🚩 Red flag #1: The page looked like a default vendor template.
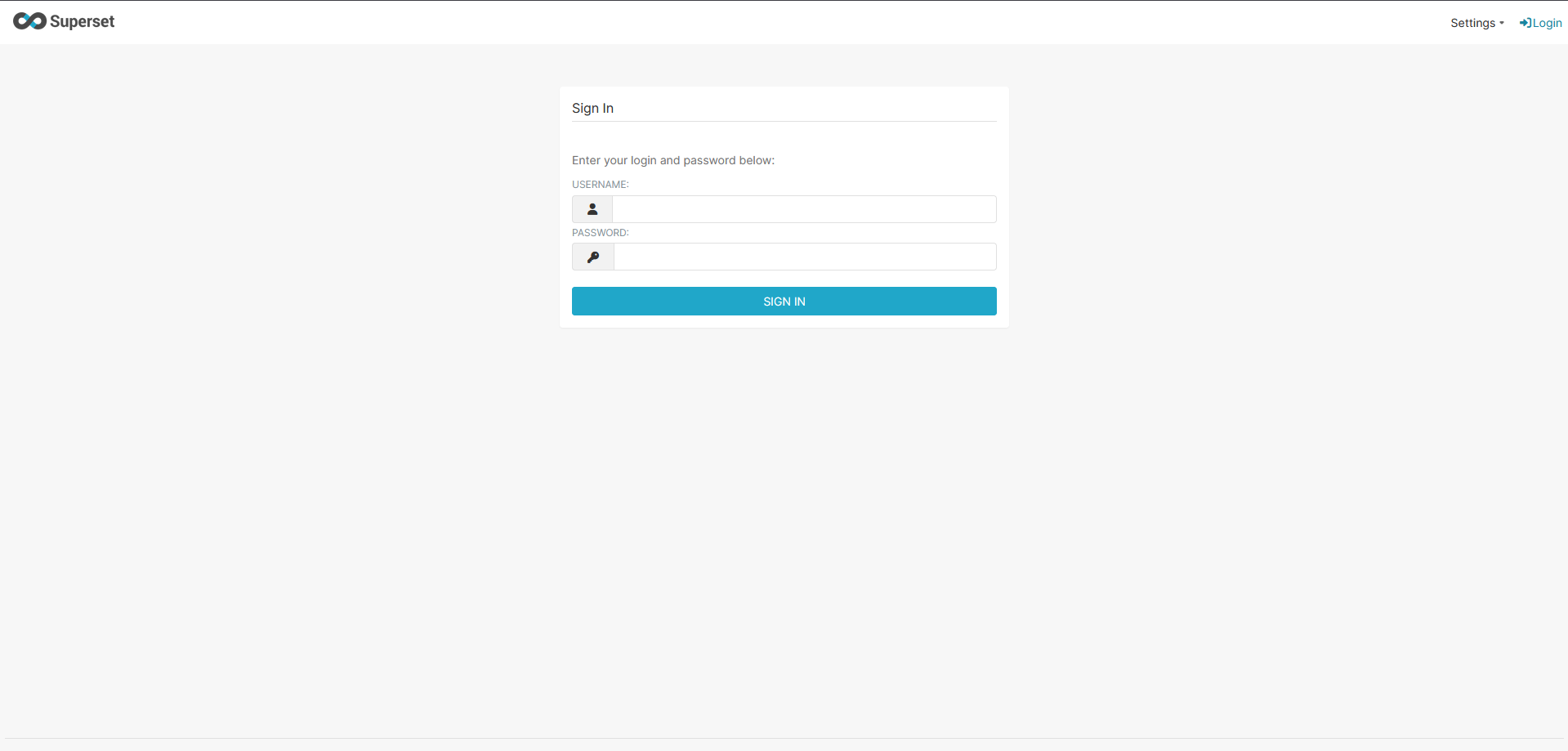
Most hackers start with complex exploits. I decided to try the easiest attack possible:
Username: admin
Password: admin
I hit Enter—and the page loaded
🚩 Red flag #2: No 2FA, no lockout policy. Just full access.

Once logged in, I had complete control over:
HR Analytics
Employees Record
Management Dashboard
There is functionality to run SQL queries and got all data from dashboard
You’d think companies would learn by now, but default credentials remain one of the top causes of breaches. Here’s why:
Laziness in Deployement
Overconfidence in Security
Vendor Negligence
Change Default Credentials Immediately
Enforce Multi-Factor Authentication (MFA)
Monitor Login Attempts
Regular Security Audits